User authentication and access#
Manage users from the administrator panel#
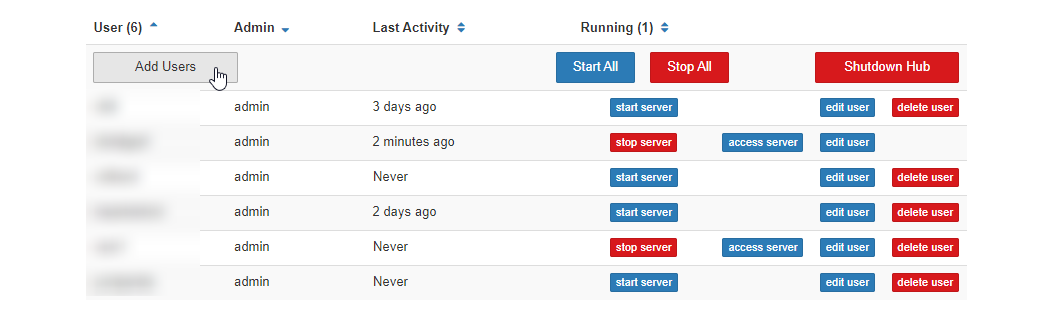
The Administrator Panel can be used to maintain the list of users
who are authorized to use your hub. You can access this panel by clicking
the ‘Admin’ button in the top bar in your hub control panel.
Alternatively, you can go to this URL in your browser:
https://<your-hub-url>/hub/admin
To add users#
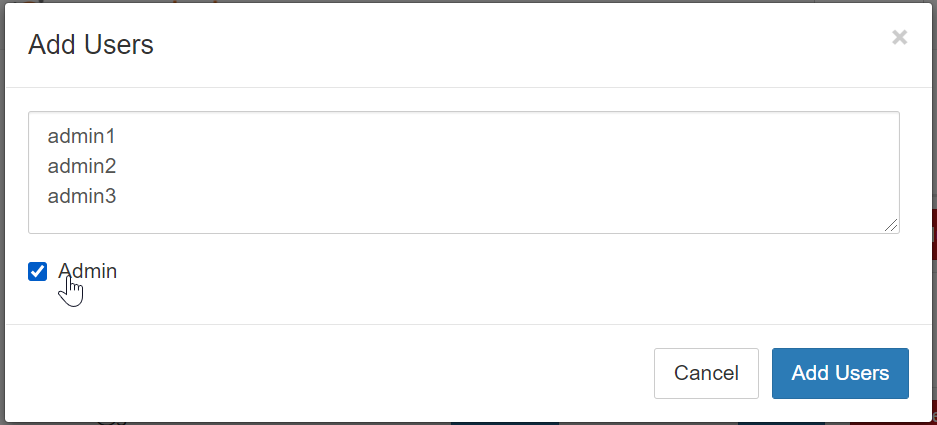
Click the Add Users button. The Add Users dialog box will pop up.
Add one or more users, and hit the Add Users button to authorize all the users you just added.
Remove users from a hub#
You can revoke a user’s access to the JupyterHub by removing them from the allowed users list, using the admin panel.
Find the name of the user in your admin panel. If they have a running server, click the Stop server button to stop their running server.
Click the Delete user button for this user. Confirm the deletion in the dialog box that pops up.
After this, the user would not be able to log in. However, their files will not be deleted - if you add them later, their files will still be present.
Finding usernames#
Access is granted or revoked based on usernames, and these depend on the kind
of authentication provider your hub is
using. In general, it matches whatever the visible ‘username’ in your
authentication provider is. The table below lists the available providers, and
how to determine their username.
Provider |
Username |
|---|---|
Email address |
|
GitHub |
GitHub user name |
Debug user authentication issues#
If users are running into strange errors when they log in (for example CILogon error pages that say “Looks like something went wrong!”), ask them to try these steps in debugging:
Try logging in with an
incognitowindow. This will help determine if their issue is due to some cookie / cache that is stored on their machine.Ask them to clear their cookies / cache for all CILogon websites. For example, here are the Google Chrome instructions to clear cookies.
If using
CILogon, double-check that they’ve signed in with the correct account, and ask them to switch accounts if needed.